Security for Endpoints
New ransomware variants and other zero-day threads routinely bypass traditional AV/antimalware security.
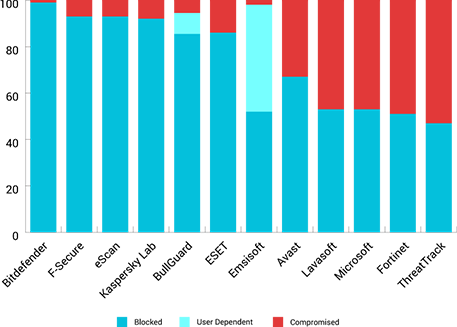
Using advanced behavior-based technologies, Bitdefender detects 99% of unknown threads in independent trails run by reputed independent testing organization, AV-Comparatives, Bitdefender also has two additional anti-ransomware defense layers - a blacklist of 2.8 million samples and rising, and a vaccine that can imminize devices against the encryption process.
Key Benefits
Easy to deploy accelerates implementation and lowers cost
Delivered as a Linux Ubuntu self-configuring hardened virtual appliance, integrates with VMware vCenter, Citrix XenServer, and Active Directory.
High availability and performance
GravityZone Security for Endpoints is delivered within a virtual appliance with built-in redundancy to minimize risks and performance issues when managing large environments, and drastically reduces the manual effort and hardware needed to maintain an enterprise-wide security system.
Scalable and resilient security
Eliminates single point of failure and AV storms; grows organically by cloning virtual appliances and automating deployment with golden images.
Simplified security management
GravityZone Security for Endpoints simplifies security operations, reduces the time required to manage and maintain security operations and further streamlines security management workflows.
Breakthrough resource optimization for physical machines
Security offloading for all types of endpoints in laptops and desktops.
Wide operating system coverage
Windows Workstation, Embedded, Server, Mac and major Linux distributions

 080-41516791
080-41516791 SALES@PERITASSOL.COM
SALES@PERITASSOL.COM